By IP Source
Residential Proxies
Residential proxies route traffic through real household devices with ISP-issued IPs. This gives them high trust and a lower chance of being flagged, making them ideal for scraping or market intelligence.
ISP (Static Residential) Proxies
ISP proxies are issued by internet providers but hosted on data center infrastructure. They combine residential legitimacy with datacenter reliability, staying static for long sessions without interruption.
Datacenter Proxies
Datacenter proxies use IPs provided by data centers rather than internet service providers. They’re extremely fast and cost-efficient, but their artificial origins make them easier for websites to detect.
Mobile Proxies
Mobile proxies run through 3G, 4G, or 5G connections provided by mobile carriers. Their IPs rotate naturally under CGNAT, making them one of the most effective options for avoiding bans or CAPTCHAs.
By Protocol
HTTP Proxies
HTTP proxies handle unencrypted web traffic, often used for caching or controlling access in internal networks. They’re simple and efficient for handling regular web requests.
HTTPS Proxies
HTTPS proxies support encrypted SSL/TLS connections, adding a layer of security to data transmission. They’re used when privacy and authentication are crucial, such as for secure logins or financial data.
SOCKS5 Proxies
SOCKS5 proxies work at a lower network level, forwarding all kinds of traffic—from web and app data to streaming and P2P. They don’t interpret the data, making them versatile but slightly slower for web-only tasks.
By Anonymity
Transparent Proxies
Transparent proxies reveal both the user’s IP and the fact that a proxy is being used. They’re typically deployed for internal filtering or caching rather than privacy.
Anonymous Proxies
Anonymous proxies hide the user’s IP but still identify themselves as proxies. They provide moderate privacy for users who don’t need complete invisibility.
Elite (High-Anonymity) Proxies
Elite proxies conceal both the user’s IP address and the proxy’s presence entirely. They’re best for stealth tasks like large-scale data collection or competitive research.
By the Access Model
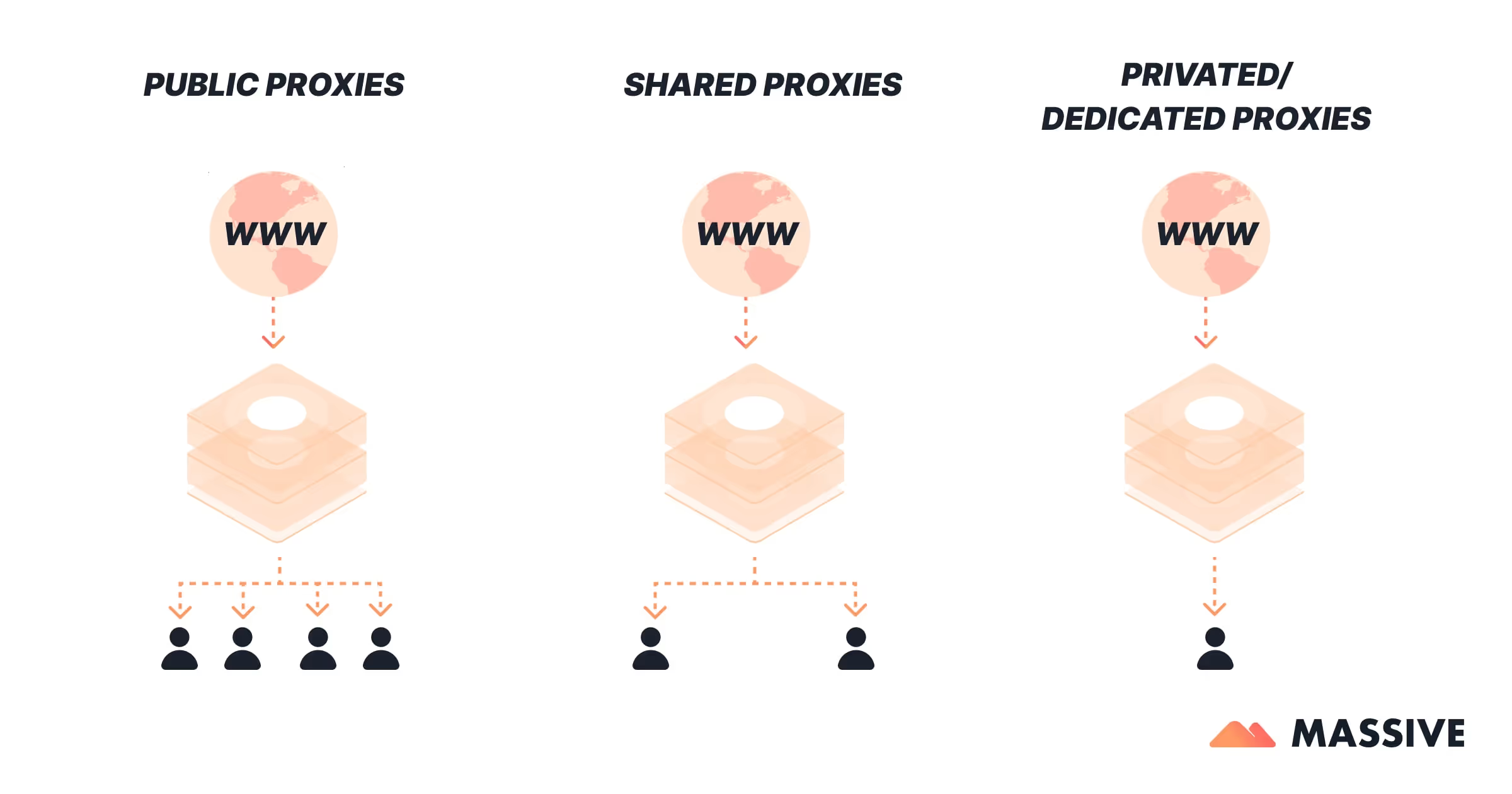
Public (Open) Proxies
Public proxies are free to use but come with major risks — they’re often slow, unstable, and may record user data. They’re suitable only for testing or learning environments.
Shared Proxies
Shared proxies are used by multiple customers at once, making them affordable and easy to scale. However, their shared nature can result in IP bans or inconsistent performance.
Private (Dedicated) Proxies
Private proxies are reserved for one user only, ensuring consistent speed and reputation. They’re the preferred choice for secure operations like managing social accounts or payment processing.
By Rotation and Session
Rotating (Backconnect) Proxies
Rotating proxies automatically switch IP addresses after each request or after a time interval. This makes them ideal for scraping large volumes of data without being blocked.
Static (Sticky) Proxies
Static proxies maintain the same IP for a set duration—usually minutes or hours. They’re perfect for tasks that require persistent sessions, such as logging into websites or maintaining shopping carts.
What Are Proxies Used For?
Proxies are used anywhere you need controlled, flexible, or anonymized access to the web. From collecting market data at scale to verifying ads in specific locations, they help teams simulate real users, avoid blocks, and access accurate, unfiltered information.
Benefits of Using Multiple Proxy Types in a Project
Using more than one proxy type lets you match each task to the best tool: speed from datacenter, trust from residential, stability from ISP, and stealth from mobile. This blended approach reduces block rates, improves data quality, and creates a more resilient workflow overall.
What’s your use case?
Chat with one of our Data Nerds and unlock a 2GB free trial tailored to your project.
Use Cases
Datacenter Proxies
Best for speed-demanding projects like bulk scraping, SEO data extraction, or traffic testing where cost and performance matter more than stealth.
Residential Proxies
Ideal for localized research, price comparison, or monitoring consumer platforms that flag datacenter traffic. Their realism keeps them under the radar.
ISP Proxies
Perfect for automation, e-commerce monitoring, and account-based workflows where long, stable sessions are necessary.
Mobile Proxies
Essential for mobile app testing, ad verification, or managing social accounts that depend on authentic mobile traffic.
Shared vs. Private Proxies
Shared proxies suit light, disposable tasks, while private proxies offer control and trust for operations that can’t afford IP bans.
Best Practices
Match Type to Task
Use datacenter proxies for speed, residential for trust, and ISP or mobile when stability and stealth are equally important.
Rotate When Needed
Employ rotating proxies for large-scale data collection, but stick to static IPs for accounts and sessions that require consistency.
Avoid Free or Public Options
Public proxies are rarely safe or reliable. Opt for trusted providers with verified IP sourcing and transparent policies.
Monitor Performance
Track latency, success rate, and block frequency. A clean, fast, and stable IP pool is better than raw quantity.
Use the Right Protocol
HTTP for general web tasks, HTTPS for secure operations, and SOCKS5 when handling non-web or multi-protocol traffic.
Conclusion
Each type of proxy serves a unique purpose—datacenter proxies deliver speed, residential and ISP proxies provide trust, and mobile proxies ensure stealth. Understanding these categories helps you build efficient, compliant, and scalable systems for data collection, automation, and testing.
Ready to power up your data collection?
Sign up now and put our proxy network to work for you.
Frequently Asked Question
What are proxies used for?
+
Monitoring prices and inventory, verifying ads, managing social accounts, testing apps from real locations, accessing geo-restricted experiences, improving privacy, and enabling corporate filtering/caching.
Which proxy type is “best”?
+
There’s no universal best—choose based on task: speed (datacenter), trust/stability (ISP or residential), mobile-app parity (mobile), protocol flexibility (SOCKS5), and use dedicated IPs when reputation consistency matters.
Are public (free) proxies safe?
+
Generally no. They’re often slow, unstable, and may log traffic or inject risks. Use vetted private/shared/dedicated options instead.
Shared vs. private/dedicated proxies—what’s the difference?
+
Shared IPs are used by many customers (cheaper but noisier reputation). Private (Dedicated) IPs are reserved for you, giving more consistent deliverability and fewer neighbor effects—ideal for logins, payments, and long-lived accounts.
What are the benefits of using multiple proxy types in a project?
+
Combining different types, like datacenter for speed, residential for trust, and mobile for resilience, gives you stronger coverage and fewer blocks. Each proxy type solves a different challenge, and using several together creates a smoother, more efficient workflow.
