An HTTP proxy sits between a client (like your browser) and the web server. When you make an HTTP request, it first goes to the proxy, which in turn contacts the target server, receives the response, and forwards it back to you.
Proxies can enhance browsing by:
- Hiding IP addresses, providing anonymity and privacy.
- Filtering content, blocking malicious material, or controlling access by scanning and enforcing policies.
- Caching frequently accessed content, speeding up browsing, and reducing bandwidth usage.
- Improving security by blocking threats before they reach internal networks.
- Optimizing performance through compression and cached response serving.
How Does an HTTP Proxy Work?
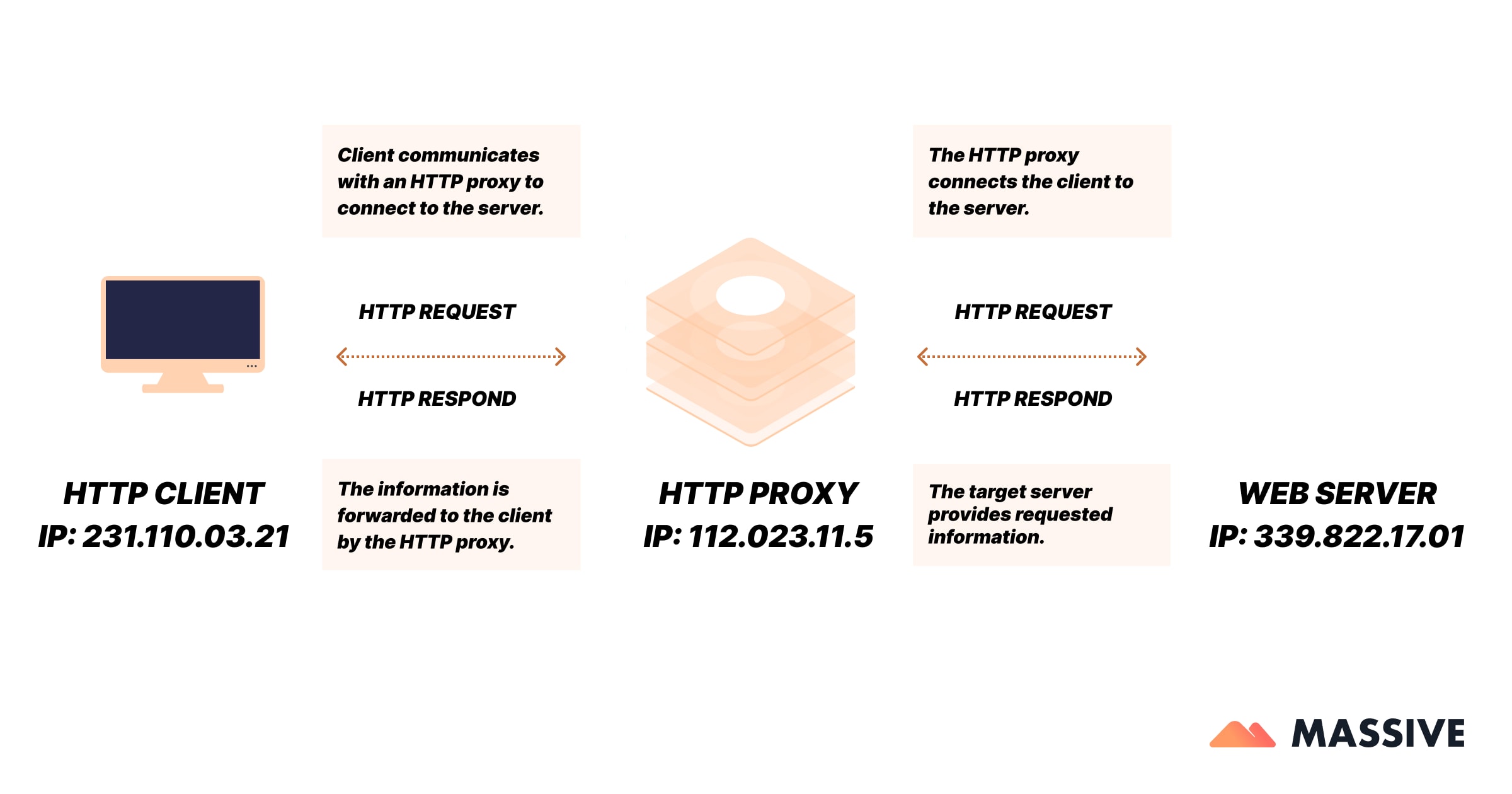
- Client Request: You attempt to access a website.
- Proxy Intercept: The request goes to the HTTP proxy.
- Forwarding: The proxy forwards the request to the actual web server.
- Response Handling: The web server responds; the proxy receives it.
- Post-Processing: Proxy may filter, cache, compress, or anonymize the response
- Delivery Back: Finally, the proxy sends the response back to you—the client.
Types of HTTP Proxies
- Forward Proxy: The typical use—client-side, for anonymity, filtering, or caching
- Transparent Proxy: Intercepts traffic without user configuration; users and servers may detect its presence
- High-Anonymity Proxy: Conceals your IP and doesn’t reveal that it’s a proxy
- Reverse Proxy: Sits in front of web servers, shielding and optimizing access to them (not primarily for client anonymity)
What’s your use case?
Chat with one of our Data Nerds and unlock a 2GB free trial tailored to your project.
Use Cases
- Improving Privacy: Users mask their IP to browse anonymously or access content without revealing their identity.
- Content Filtering: In schools or workplaces, proxies block access to restricted sites using URL or MIME type filtering.
- Caching for Speed: Enterprises cache popular pages to reduce loading times and save bandwidth.
- Bypassing Geo-Restrictions: Access region-blocked content by routing requests through a proxy in a different location.
- Enhanced Security: Blocking malware, detecting intrusions, or denying downloads of unsafe file types.
- Web Scraping & Automation: Bots and crawlers can rotate through proxies to avoid IP-based blocking.
- Reverse Proxy Management: Websites use reverse proxies for load balancing, caching, and shielding internal infrastructure.
Best Practices
- Enable Caching Wisely: Use appropriate headers (Cache-Control, Expires) to balance performance with content freshness.
- Set Clear Filtering Rules: Customize content policies—block unsafe domains, file types, or large requests.
- Use HTTPS When Needed: HTTP proxy doesn’t provide encryption; use HTTPS or specialized HTTPS proxies for secure data.
- Handle Authentication Carefully: For transparent proxies, ensure users are aware or provide clear notifications.
- Log Responsibly: Protect user privacy—avoid unnecessary capture of sensitive data when implementing logging.
- Monitor Performance: Proxies can introduce latency—regularly test network performance to ensure smooth operation.
- Protect the Proxy Itself: Secure and update proxy software to avoid it becoming an attack surface.
- Transparency vs. Anonymity: Choose proxy type based on needs—transparency for internal control, high-anonymity for privacy
Conclusion
An HTTP proxy is an intermediary server that forwards web requests and responses, often adding features like caching, filtering, or anonymization. It improves privacy, security, and performance while enabling access control and tunneling for secure HTTPS traffic.
Ready to power up your data collection?
Sign up now and put our proxy network to work for you.
Frequently Asked Question
If I connect to a proxy server with HTTP but send an HTTPS request, is my data secure?
+
Yes. When you send an HTTPS request through an HTTP proxy, your browser first establishes an encrypted HTTPS tunnel using the CONNECT method. The proxy passes encrypted bytes back and forth without interpreting them. This means the proxy cannot see your headers, body content, or sensitive data—it only sees the destination domain (e.g., https://example.com:443) needed to route the traffic.
The only risk is if the proxy itself performs a man-in-the-middle attack by decrypting and re-encrypting your traffic with its own certificate. In that case, your browser would show warnings about an untrusted certificate. As long as you don’t ignore those warnings, your HTTPS data remains private and secure, even when routed through an HTTP proxy.
How does an HTTP proxy use the HTTP protocol?
+
An HTTP proxy communicates with web servers using standard HTTP but slightly modifies how requests are sent. Instead of sending just the path (e.g., GET / HTTP/1.1), the proxy must include the full URL (e.g., GET http://example.com/ HTTP/1.1). This allows the proxy to know which server the request is meant for.
For secure connections, the proxy uses the CONNECT method, which creates a tunnel to the destination server (usually on port 443 for HTTPS). After the tunnel is established, encrypted HTTPS traffic flows through without the proxy interpreting its content.
In short, a proxy behaves similarly to a web server—it parses client requests—but instead of processing them, it forwards them to the intended server and relays the response back. Some proxies also add caching or filtering, while others act as simple pass-through intermediaries.
What is the difference between an HTTP proxy and an HTTP tunnel?
+
HTTP Proxy: A proxy acts as an intermediary. It forwards client requests to servers and can modify or filter them. Proxies can cache responses, scan for security threats, or alter headers. They typically work with the same protocol end-to-end (HTTP in this case).
HTTP Tunnel: Tunneling is a technique that allows one protocol to be carried inside another. For example, an HTTP tunnel can encapsulate HTTPS or even non-HTTP traffic like FTP or SOCKS. The proxy uses the CONNECT method to establish a tunnel, which is especially common for HTTPS connections on port 443.
