What Does a Proxy Server Do?
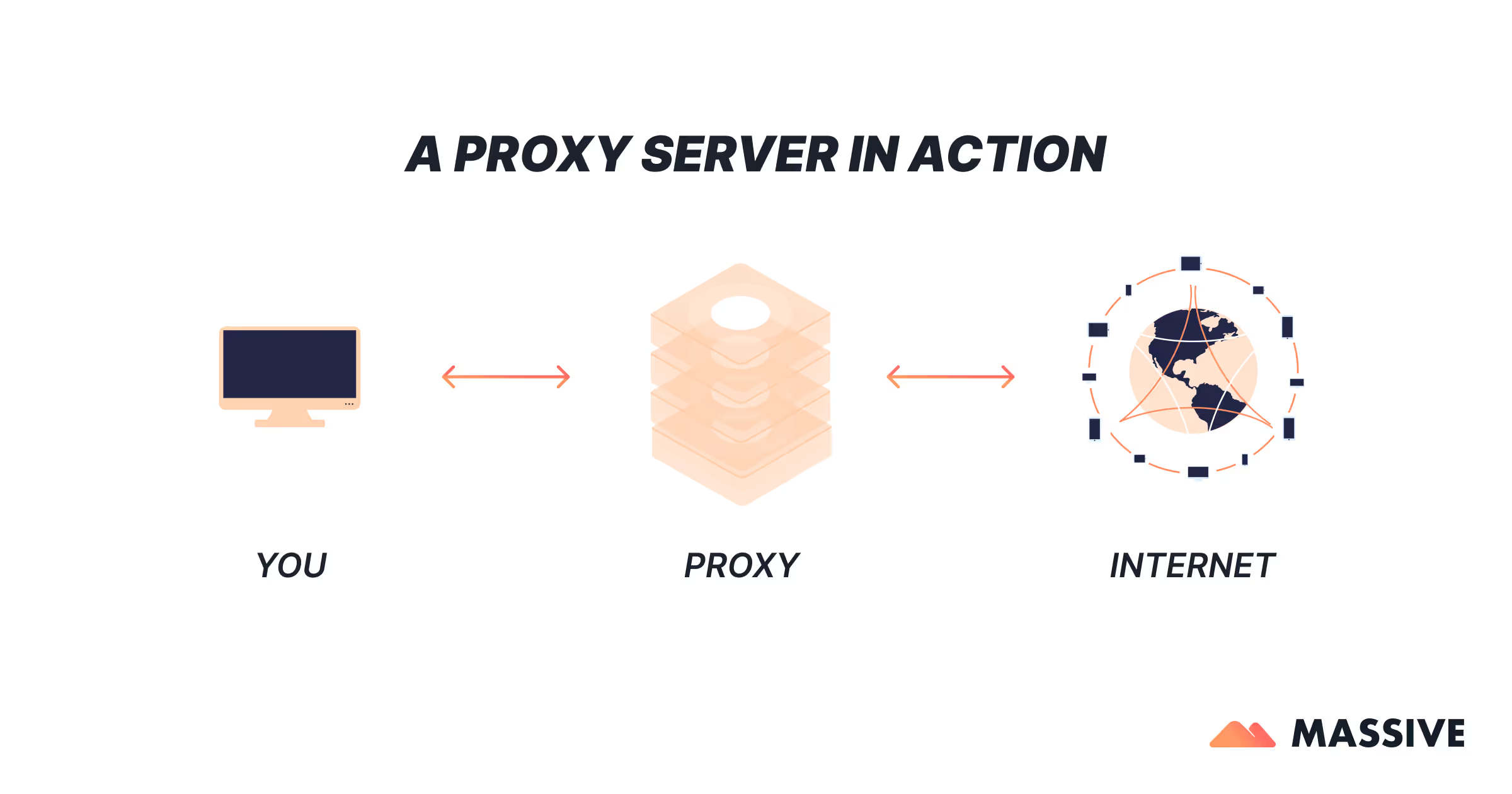
Think of a proxy server like having someone run errands on your behalf. Instead of you going straight to the store, you ask a helper (the proxy) to go get what you need and bring it back. In networking, your phone, laptop, or router sends requests (like “load this web page”) to the proxy, and the proxy retrieves the data before sending it back to you.
This setup can serve different purposes depending on who controls the proxy:
- Businesses often use proxies to control and secure employee internet traffic. They can block harmful websites, track browsing activity, and prevent unauthorized access.
- Individuals sometimes use proxies to mask their real location or IP address, allowing access to region-restricted content (like streaming sites).
- ISPs, schools, and organizations may run proxies to enforce policies, improve security, or optimize traffic.
Unlike a VPN, which encrypts all of your traffic, proxies don’t necessarily provide full privacy or security—they mainly act as a routing and filtering layer.
In practice, this is how a proxy server works—it intercepts, forwards, and manages requests, acting as a filter, cache, or controller depending on its type of proxy (HTTP, SOCKS5, or reverse proxy).
¿Cuál es tu caso de uso?
Chatea con uno de nuestros fanáticos de los datos y desbloquea una prueba gratuita de 2 GB adaptada a tu proyecto.
Use Cases
What Is The Purpose of a Proxy Server?
A proxy server can serve multiple purposes—protecting networks, managing access, improving performance, and preserving privacy. How it’s used depends on who controls it and what goals they want to achieve.
The purpose of a proxy server depends on context—from securing corporate networks and managing user access to accelerating content delivery and anonymizing traffic.
1. Security and Filtering
Proxies block access to malicious websites, phishing pages, and untrusted content. Businesses often rely on them to protect employees from threats or data leaks, while schools use them to restrict inappropriate material.
2. Compliance and Monitoring
Organizations in finance, healthcare, and education use proxies to log activity, enforce policies, and meet strict compliance standards. They can track browsing behavior and ensure no sensitive data leaves the network.
3. Performance and Scalability
Proxies improve load times by caching popular content and offloading encryption or decryption tasks. For example, large-scale services use reverse proxies to balance user traffic and prevent server overload.
4. Privacy and Anonymity
Forward proxies can hide a user’s IP address, making browsing activity less traceable. Individuals use them to bypass geo-restrictions or browse anonymously without exposing their real location.
5. Centralized Control
IT administrators use proxies to apply consistent rules across all devices—deciding who can access what and when. This simplifies network management and improves visibility across large systems.
Best Practices
Know Your Purpose
As a regular user, you probably don’t need a proxy unless your workplace or a specific tool requires it. Businesses, however, benefit from the visibility and control proxies provide.
Use Trusted Providers
Avoid free or unknown proxies—they often log your traffic and can compromise your security. Choose reputable proxy services with clear privacy policies.
Don’t Rely on Proxies Alone for Privacy
Proxies don’t encrypt your data like VPNs do. Use them alongside HTTPS or VPNs for full protection.
Optimize Configuration
Set proxies at the right level—browser-level proxies only affect web traffic, while network-level proxies can manage all device connections. For business environments, monitor proxy cache size and bandwidth performance regularly. Overloaded or outdated proxies can slow down connections and reduce efficiency.
Combine with Other Security Layers
Proxies work best as part of a broader security setup that includes firewalls, VPNs, and encryption.
Conclusion
A proxy server is more than just an internet go-between—it’s a tool that enhances privacy, security, and efficiency when used correctly. Whether protecting employees, improving performance, or accessing blocked content, proxies serve many purposes across networks and users. The key is to choose the right type of proxy and configure it securely to maximize benefits without creating new risks.
Ready to power up your data collection?
Sign up now and put our proxy network to work for you.
Frequently Asked Question
How do proxy servers work?
+
A proxy server acts as an intermediary between your device and the internet. When you request a web page, your device sends the request to the proxy instead of the destination site. The proxy then forwards that request, retrieves the content, and returns it to you. This process allows the proxy to filter or cache data, log activity, enforce policies, or mask your IP address for privacy and control.
What is a common function of a proxy server?
+
The most common function of a proxy server is to manage and control the flow of data between users and the internet. It can hide IP addresses, filter web traffic, cache frequently accessed resources for faster load times, and block unsafe or restricted content. In business environments, proxies also help with security, compliance, and network optimization.
How does a proxy server improve security?
+
Proxies improve security by acting as a protective barrier between users and the web. They can block access to malicious or untrusted websites, filter out harmful content, and prevent direct communication with potentially dangerous servers. Some advanced proxies also perform SSL inspection to detect hidden threats within encrypted traffic, while IP masking helps reduce exposure to cyberattacks.
Should I use a proxy server?
+
You should use a proxy server if you need additional privacy, security control, or access to restricted content. Businesses often use them to monitor employee traffic and enforce network policies, while individuals use them to browse anonymously or bypass geo-blocks. However, for full encryption and data protection, pairing a proxy with a VPN is often the better choice.
What is a proxy server definition?
+
A proxy server is a computer system or router that serves as a gateway between users and the internet. It prevents direct connections between a device and external servers, hiding internal IP addresses and filtering network traffic. In short, it defines a controlled way for data to enter and leave a network securely.
